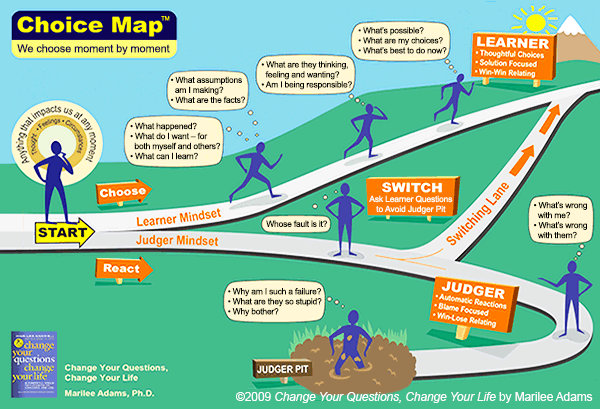
42 identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used.
› Tags › SatelliteSatellite News and latest stories | The Jerusalem Post Mar 08, 2022 · Breaking news about Satellite from The Jerusalem Post. Read the latest updates on Satellite including articles, videos, opinions and more. talkingpointsmemo.com › muckrakerCategory: Muckraker - TPM – Talking Points Memo Aug 26, 2022 · A Legal Filing Sheds Some Light On What May Have Happened To All Those Jan. 6 Text Messages
› subscribeSubscribe - RFID JOURNAL Only RFID Journal provides you with the latest insights into what’s happening with the technology and standards and inside the operations of leading early adopters across all industries and around the world. To stay informed and take advantage of all of the unique resources RFID Journal offers become a member today.

Identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used.
same access through those ports Spanning tree Spanning tree is a ... [All Questions SecPro2017_v6.exm SWITCH_SECURITY_07] [All Questions SecPro2017_v6.exm SWITCH_SECURITY_07] Question 61: Question 61: Incorrect Incorrect Identify and label the following attacks by dragging the term on the left to the definition on the Identify and label the following attacks by dragging the term on the left to the definition on ... Dystonias Fact Sheet | National Institute of Neurological Disorders and ... Idiopathic dystonia refers to dystonia that does not have a clear cause. Many instances of dystonia are idiopathic. There are several genetic causes of dystonia. Symptoms may vary widely in type and severity even among members of the same family. In some instances, people who inherit the defective gene may not develop dystonia. Anatomy Terms - Health Pages The most widely used regional terms used are those that describe the 9 abdominal regions shown in the image to the right. The regions are named below and the corresponding regions are labeled 1-9. Abdominal Regions. Right (1) and left (3) hypochondriac regions - on either side of the epigastric region. Contains the diaphragm, some of the ...
Identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used.. en.wikipedia.org › wiki › Antisemitism_in_the_UKAntisemitism in the UK Labour Party - Wikipedia In his 2012 book, The British Left and Zionism: History of a Divorce, Manchester University's Paul Kelemen ascribed the shift in Labour's views to Israel's increasingly right-leaning politics and to the left's opposition to the Israeli occupation of the West Bank and Gaza. He found no evidence that antisemitism played a role in the left's ... Terrorism — FBI - Federal Bureau of Investigation To counter terrorism, the FBI's top investigative priority, we use our investigative and intelligence capabilities to neutralize domestic extremists and help dismantle terrorist networks worldwide. ReaderUi ReaderUi For detecting rogue hosts include for detecting rogue Identify and label the following attacks by dragging the term on the left to the definition on the Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. right. Not all terms are used.
Solved Match each term to the corresponding definition. Drag | Chegg.com Transcribed image text: Match each term to the corresponding definition. Drag each item on the left to its matching item on the right. rate of interest paid by private banks to the Fed money lent by the Fed to private banks discount rate" open market operations reserve requirement discount loans the amount of deposits a bank must hold in reserve and cannot lend the purchase or sale of bonds ... Label the heart — Science Learning Hub In this interactive, you can label parts of the human heart. Drag and drop the text labels onto the boxes next to the diagram. Selecting or hovering over a box will highlight each area in the diagram. pulmonary vein. semilunar valve. right ventricle. right atrium. vena cava. left atrium. EOF Test Out 3 - Subjecto.com You identify the following values: • Asset value = 400 ... Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. Vishing Piggybacking Spam Phishing Whaling
3.5 Flashcards | Quizlet Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. 1) An attacker convinces personnel to grant access to sensitive information or protected systems by pretending to be someone who is authorized and/or requires that access. Masquerading, › sectionSection - Jamaica Observer Breaking news from the premier Jamaican newspaper, the Jamaica Observer. Follow Jamaican news online for free and stay informed on what's happening in the Caribbean Match each description to its corresponding term. (Not all options are ... IT Questions Bank › Category: CCNA CyberOps › Match each description to its corresponding term. (Not all options are used.) Match each description to its corresponding term. (Not all options are used.) message encoding : the process of converting information from one format into another acceptable for transmission. en.wikipedia.org › wiki › VampireVampire - Wikipedia The term vampire did not exist in ancient times. Blood drinking and similar activities were attributed to demons or spirits who would eat flesh and drink blood; even the devil was considered synonymous with the vampire. Almost every culture associates blood drinking with some kind of revenant or demon, or in some cases a deity.
ceufast.com › course › annual-requirements-updateAnnual Regulatory Requirements, Current Practice | HIPAA ... Medication to control behavior should be used only as part of a therapeutic plan, after appropriate assessment by professionals. Chemical restraint is a term used to describe the use of medications for purposes unrelated to the client’s medical condition. An example is the use of a sedating psychotropic drug to manage or control behavior.
Threats, Attacks, and Vulnerabilities Flashcards | Quizlet A virusvirus is a program that attempts to damage a computer system and replicate itself to other computer systems. A wormworm is a self-replicating program that can be designed to do any number of things, such as negatively impacting network traffic. A Trojan horseTrojan horse is a malicious program that is disguised as legitimate software.
Anatomy Terms - Health Pages The most widely used regional terms used are those that describe the 9 abdominal regions shown in the image to the right. The regions are named below and the corresponding regions are labeled 1-9. Abdominal Regions. Right (1) and left (3) hypochondriac regions - on either side of the epigastric region. Contains the diaphragm, some of the ...
Dystonias Fact Sheet | National Institute of Neurological Disorders and ... Idiopathic dystonia refers to dystonia that does not have a clear cause. Many instances of dystonia are idiopathic. There are several genetic causes of dystonia. Symptoms may vary widely in type and severity even among members of the same family. In some instances, people who inherit the defective gene may not develop dystonia.
same access through those ports Spanning tree Spanning tree is a ... [All Questions SecPro2017_v6.exm SWITCH_SECURITY_07] [All Questions SecPro2017_v6.exm SWITCH_SECURITY_07] Question 61: Question 61: Incorrect Incorrect Identify and label the following attacks by dragging the term on the left to the definition on the Identify and label the following attacks by dragging the term on the left to the definition on ...



















Post a Comment for "42 identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used."